Cyber-Security is much more than a matter of IT.
Stephane Nappo
Cyber Security at the Next Level: Focus on Digital Transformation
With the reproduction of Internet-enabled devices, cyber culture is flourishing more rapidly than cyber security. Everything that depends on cyberspace is possibly at risk. The new technologies of today’s dynamic digital world, such as IoT, cloud computing, and the interconnected supply chain, bring a new level of uncertainty, but also new possibilities. Moreover, Intellectual property, private data, cyberinfrastructure & even military and national security can be compromised by regular attacks, accidental security failures, and the vulnerabilities of a nearly immature, unchecked global Internet.
In an ever-changing cyber landscape, the only certainty is that cybercrime will continue to grow. So, To tackle new & modifying threats, what are the critical technology trends that cyber leaders will lean on?
Acknowledging the cyber risk of an organization requires knowledge of the operational processes. Further, Business models, maturity levels, trends, and vulnerabilities particular to that organization & normally present in its industry sector.
Securing exclusive information & other critical business strong point becomes more difficult & meeting regulatory requirements is more complex. Furthermore, In an era where cyber is everywhere, it’s possible to invest in cyber security controls and preventive measures to ensure you can take your business anywhere.
Also Read: Digital Transformation In Marketing : Strategies, Practices
Assessing the Likelihood of a cyber security Attack
It’s a quiet Sunday night. Suddenly, the phone rings. It’s your CIO. You’ve been hacked. The hackers are frightened to tear down your company’s complete data warehouse in 24 hours unless you pay a $4 million price. Your move.
Every cyberattack is not this much drama. Often, companies don’t understand for six months or more that they’ve been compromised. But whether the attack is swiftly evident or discloses itself over time, you need to be ready.
Put an end to threats is impossible so, shielding against them without disrupting business revolution & growth is a top management issue.
The way to develop a practical & efficient cybersecurity strategy that makes the best use of the company’s investment starts with the awareness that not every data asset or application needs the same level or type of protection.
Why are so many firms now fighting cyber security attack? One reason is that as businesses grow progressively virtual, they have more regions to protect. But the important reason may be that many companies have misinterpreted the challenge.
Also Read: 21 Best Digital Transformation Books
Leader’s Tip:
Invest in cyber security knowledge: To improve their company’s cyber defence capabilities, leaders should give priority to hiring and collaborating with knowledgeable individuals.
Cyber Security-Evaluating Your Existing Defense
The first thing is to evaluate your company’s present level of cyber security strategy. We work with you to obtain a strategic view of your company’s cyber-flexibility. This includes one or more of the following options:
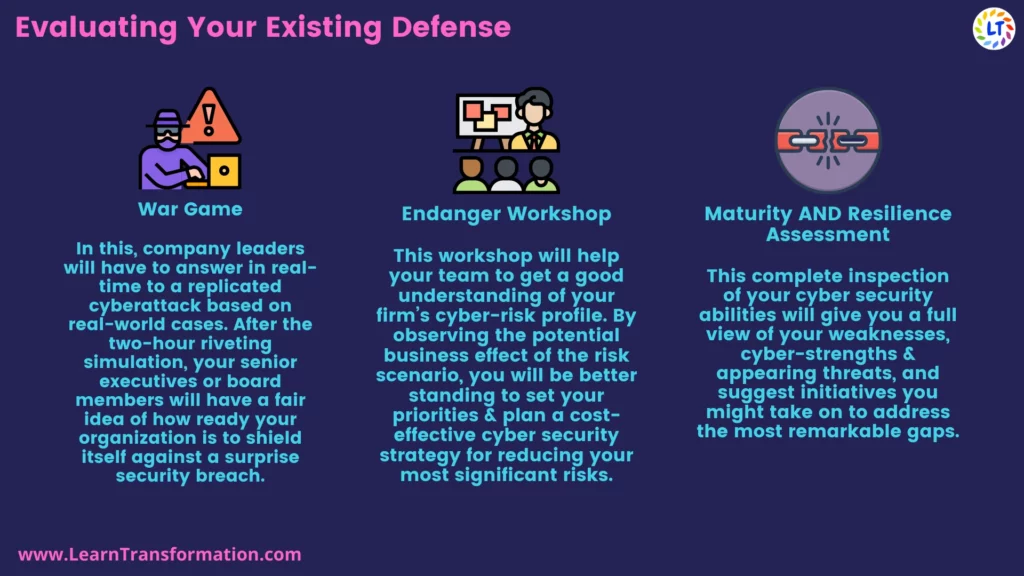
1. War Game-
In this, company leaders will have to answer in real-time to a replicated cyberattack based on real-world cases. Certainly, After the two-hour riveting simulation, your senior executives or board members will have a fair idea of how ready your organization is to shield itself against a surprise security breach.
2. Endanger Workshop-
This workshop will help your team to get a good understanding of your firm’s cyber-risk profile. Moreover, By observing the potential business effect of the risk scenario. You will be in better standing to set your priorities & plan a cost-effective cyber security strategy for reducing your most significant risks.
3. Maturity AND Resilience Assessment-
This complete inspection of your cyber security abilities will give you a full view of your weaknesses. Cyber-strengths & appearing threats, and suggest initiatives you might take on to address the most remarkable gaps.
This full cyber checkup will help you intensify your cyber-risk registry in a way that makes sure not only that you’re wrapping all the right bases but also that you are doing the right security investments. By the end of this exercise, you will be aware of the prime security-related abilities your organization owns, which it lacks, and what your next steps should be for transformation.
Check out the video –
Cyber Crime Fighting
As personal, government & commercial activities continue to drift to the digital transformation, so do criminals. Wide-ranging cyber attacks are becoming more periodic & more expensive for businesses. Attackers are better funded, more enlightened, and better sorted than in the past, often representing criminal networks or states.
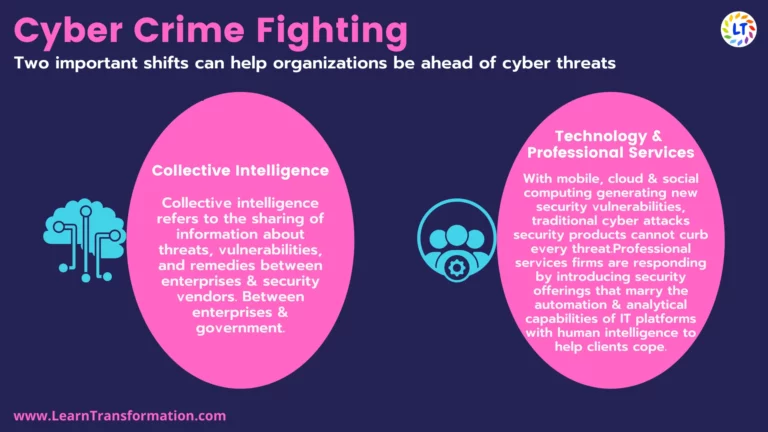
Two important shifts can help organizations be ahead of cyber threats.
1. Collective Intelligence-
- Collective intelligence refers to the sharing of information about threats, vulnerabilities, and remedies between enterprises & security vendors. Between enterprises as well as government.
- It can improve risk management by swiftly spreading knowledge of vulnerabilities and threats. It can direct cyber forensics & security audits to areas of suspected weakness.
- It can disclose trends & recommend areas where investment in additional security measures is guaranteed.
- Numerous vendors are expanding shared-intelligence features such as email addresses, introducing data feeds of unidentified & aggregated data about IP addresses, queries, file names to improve security for all of their customers.
2. Technology & Professional Services-
- With mobile, cloud & social computing generating new security vulnerabilities, traditional cyber attacks security products such as antivirus scanners & firewalls cannot curb every threat.
- Tools such as network security analyzers can be hard for some enterprises to successfully utilize without outside help.
- Professional services firms are responding by introducing security offerings that marry the automation & analytical capabilities of IT platforms with human intelligence to help clients cope. Further, Such technological contribution can help organizations collect, monitor & analyze large data sets and identify those patterns that specify breaches or attempted breaches. And, This allows organizations to respond to threats with more sharpness.
- And Lastly, Making use of collective intelligence & joining automation and analytics to human judgment can help organizations decrease the risk of a cyber-attack & lower the costs of diminishing attacks that do occur.
Leader’s Tip:
Encourage a culture of security awareness by teaching staff how to spot and respond to potential threats. Leaders must nurture this culture.
Final Word
Learn Transformation experts thinks that, Cyber security must be ‘business back’ rather than ‘technology forward’. Therefore, Companies will have to alter their thinking to address cyber risks. They should first guard the most analytical business assets or processes (such as customer credit card information)—what we think a “business-back” approach. So, Corporations have begun to analyze their cyber risk profile across the full value chain, filtering expectations with vendors & increasing collaboration with key business partners.
Frequently Asked Questions
What role does leadership play in ensuring cyber security during digital transformation?
Leadership plays a crucial role in setting the tone for cyber security awareness, allocating resources, prioritizing investments, and promoting a culture of security throughout the organization.
What are the benefits of prioritizing cyber security in digital transformation?
Prioritizing cyber security in digital transformation provides benefits such as protection against financial losses, reputational damage, regulatory penalties, and improved customer trust and loyalty.
Key Takeaways:
- Internet safety is crucial: Organisations must prioritise strong security measures as digital transformation progresses to protect sensitive data and operations.
- It is essential to play a proactive defence; leaders should monitor developing dangers, periodically evaluate their vulnerabilities, and take precautions to reduce risks.
- Working together is crucial: Organisations can share knowledge and take advantage of collective expertise by collaborating with peers in the sector and cyber security specialists to develop efficient defence plans.